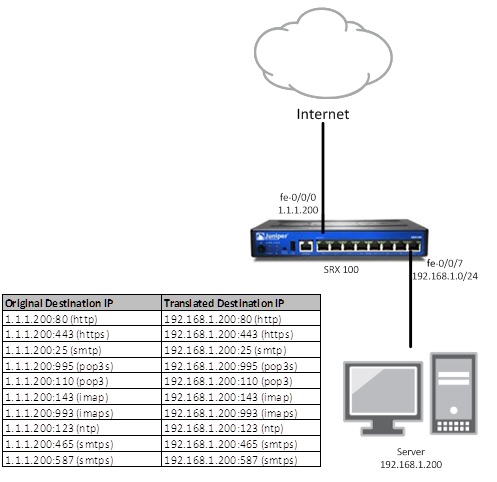
Итак, имеем почтовый и Web сервер за «роутером». Необходимо наладить его работу за NAT.
Сервер подключен в порт fe-0/0/7 ,который является членом vlan.1 (зона DMZ)
Для начала сделаем «проброс» портов «снаружи», при этом используем стандартные номера портов (т.е. трансляция порт в порт).
Сперва необходимо создать адресную запись (pool)
set security nat destination pool HTTP address 192.168.1.200/32
set security nat destination pool HTTP address port 80
set security nat destination pool HTTPS address 192.168.1.200/32
set security nat destination pool HTTPS address port 443
set security nat destination pool SMTP address 192.168.1.200/32
set security nat destination pool SMTP address port 25
set security nat destination pool POP3S address 192.168.1.200/32
set security nat destination pool POP3S address port 995
set security nat destination pool POP3 address 192.168.1.200/32
set security nat destination pool POP3 address port 110
set security nat destination pool IMAP address 192.168.1.200/32
set security nat destination pool IMAP address port 143
set security nat destination pool IMAPS address 192.168.1.200/32
set security nat destination pool IMAPS address port 993
set security nat destination pool NTP address 192.168.1.200/32
set security nat destination pool NTP address port 123
set security nat destination pool SMTPs address 192.168.1.200/32
set security nat destination pool SMTPs address port 465
set security nat destination pool SMTPS address 192.168.1.200/32
set security nat destination pool SMTPS address port 587
Далее создаем rule-set, т.е. свод правил Destination NAT:
set security nat destination rule-set dst-nat from interface fe-0/0/0.0 # ну или from zone untrust
set security nat destination rule-set dst-nat rule HTTP match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule HTTP match destination-port 80
set security nat destination rule-set dst-nat rule HTTP then destination-nat pool HTTP
set security nat destination rule-set dst-nat rule HTTPs match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule HTTPs match destination-port 443
set security nat destination rule-set dst-nat rule HTTPs then destination-nat pool HTTPS
set security nat destination rule-set dst-nat rule SMTP match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule SMTP match destination-port 25
set security nat destination rule-set dst-nat rule SMTP then destination-nat pool SMTP
set security nat destination rule-set dst-nat rule POP3S match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule POP3S match destination-port 995
set security nat destination rule-set dst-nat rule POP3S then destination-nat pool POP3S
set security nat destination rule-set dst-nat rule POP3 match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule POP3 match destination-port 110
set security nat destination rule-set dst-nat rule POP3 then destination-nat pool POP3
set security nat destination rule-set dst-nat rule IMAP match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule IMAP match destination-port 143
set security nat destination rule-set dst-nat rule IMAP then destination-nat pool IMAP
set security nat destination rule-set dst-nat rule IMAPS match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule IMAPS match destination-port 993
set security nat destination rule-set dst-nat rule IMAPS then destination-nat pool IMAPS
set security nat destination rule-set dst-nat rule NTP match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule NTP match destination-port 123
set security nat destination rule-set dst-nat rule NTP then destination-nat pool NTP
set security nat destination rule-set dst-nat rule SMTPs match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule SMTPs match destination-port 465
set security nat destination rule-set dst-nat rule SMTPs then destination-nat pool SMTPs
set security nat destination rule-set dst-nat rule SMTPS match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule SMTPS match destination-port 587
set security nat destination rule-set dst-nat rule SMTPS then destination-nat pool SMTPS
Создаем NAT для сервера
set security nat source rule-set DMZ-to-untrust from zone DMZ
set security nat source rule-set DMZ-to-untrust to zone untrust
set security nat source rule-set DMZ-to-untrust rule SNAT-DMZ-untrust match source-address 192.168.1.0/24
set security nat source rule-set DMZ-to-untrust rule SNAT-DMZ-untrust match destination-address 0.0.0.0/0
set security nat source rule-set DMZ-to-untrust rule SNAT-DMZ-untrust then source-nat interface
Создаем политику доступа к серверу.
set security address-book global address DMZ-Server 192.168.1.200/32
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match source-address any
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match destination-address DMZ-Server
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ match application any
set security policies from-zone untrust to-zone DMZ policy untrust-to-DMZ then permit
set security policies from-zone DMZ to-zone untrust policy DMZ-to-untrust match source-address any
set security policies from-zone DMZ to-zone untrust policy DMZ-to-untrust match destination-address any
set security policies from-zone DMZ to-zone untrust policy DMZ-to-untrust match application any
set security policies from-zone DMZ to-zone untrust policy DMZ-to-untrust then permit
set security zones security-zone DMZ description «DMZ zone»
set security zones security-zone DMZ host-inbound-traffic system-services all
set security zones security-zone DMZ host-inbound-traffic protocols all
set security zones security-zone DMZ interfaces vlan.1
Собственно на этом настройка закончена. Жмем commit и наслаждаемся 🙂
Второй вариант (упрощенный) «проброса» портов на сервер в trust зоне. Допустим у нас один VLAN с порта fe-0/0/1 и до fe-0/0/7, при этом порт WAN — fe-0/0/0 (как на рисунке)
Нужно обеспечить доступность сервера извне по двум портам 80 и 443.
set security nat destination pool HTTP address 192.168.1.200/32
set security nat destination pool HTTP address port 80
set security nat destination pool HTTPS address 192.168.1.200/32
set security nat destination pool HTTPS address port 443
set security nat destination rule-set dst-nat from zone untrust
set security nat destination rule-set dst-nat rule HTTP match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule HTTP match destination-port 80
set security nat destination rule-set dst-nat rule HTTP then destination-nat pool HTTP
set security nat destination rule-set dst-nat rule HTTPs match destination-address 1.1.1.200/32
set security nat destination rule-set dst-nat rule HTTPs match destination-port 443
set security nat destination rule-set dst-nat rule HTTPs then destination-nat pool HTTPS
set security zones security-zone trust address-book address server 192.168.1.200/32
set security policies from-zone untrust to-zone trust policy untrust-to-trust2 match source-address any
set security policies from-zone untrust to-zone trust policy untrust-to-trust2 match destination-address server
set security policies from-zone untrust to-zone trust policy untrust-to-trust2 match application https
set security policies from-zone untrust to-zone trust policy untrust-to-trust2 match application http
set security policies from-zone untrust to-zone trust policy untrust-to-trust2 then permit
set applications application http protocol tcp
set applications application http destination-port 80
set applications application https protocol tcp
set applications application https destination-port 443
Все, «проброс» работает.